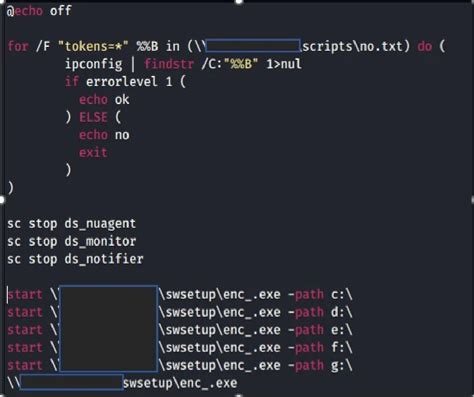
lv ransomware | lv ransomware gang revil lv ransomware CTU analysis revealed that the LV ransomware is not a distinct ransomware family; it is repurposed REvil ransomware. By modifying the binary of a prolific ransomware family, the GOLD NORTHFIELD threat actors significantly expedited their . Skateboard griptape provides firm footing and better control for skateboard tricks. Coarser griptape is ideal for higher speed skateboarding where you really want your feet to stay in place. Less coarse griptape is more ideal for street, bowl, park, and cruiser setups because you are constantly moving around on them.
0 · lv ransomware hijackers
1 · lv ransomware hacked
2 · lv ransomware gang revil
3 · lv ransomware binary
By Brian Eller Updated on February 5, 2024. The MGM Grand Buffet has one of the largest selections of classic American foods available on the Las Vegas Strip. The buffet is open seven days a week and offers breakfast, brunch, and dinner with elevated selections on the weekends.
Oct 25, 2022 Researchers have discovered that the LV ransomware that has been in use since late 2020 is actually a modified version of the REvil ransomware binary that is being . The Trend Micro research team recently analyzed an infection related to the LV ransomware group, a ransomware as a service (RaaS) operation that has been active since late 2020, and is reportedly based on REvil (aka Sodinokibi). CTU analysis revealed that the LV ransomware is not a distinct ransomware family; it is repurposed REvil ransomware. By modifying the binary of a prolific ransomware family, the GOLD NORTHFIELD threat actors significantly expedited their .
Researchers have discovered that the LV ransomware that has been in use since late 2020 is actually a modified version of the REvil ransomware binary that is being distributed by a separate threat group.
In what can be described as a case of piracy among cybercrime gangs, the LV ransomware gang appears to have hijacked and modified the binary payload of the more infamous REvil group.
German power electronics manufacturer Semikron has disclosed that it was hit by a ransomware attack that partially encrypted the company's network. Trend Micro provides a detailed analysis of an LV ransomware attack on a Jordan-based company, highlighting the attackers' methods and the wide range of targeted industries.
Researchers at Secureworks tracked what looked like a new ransomware strain, dubbed LV, which has been in the wild since late 2020, and found that it had identical code structure to REvil. In an incident, LV Ransomware compromised the corporate environment of a Jordan-based organization. It exploited the Microsoft flaws— ProxyShell and ProxyLogon —vulnerabilities and dropped a webshell in the public access folders.LV ransomware-as-a-service has been active since late 2020. The most recent infiltration entailed the compromise of the corporate environment of a Jordan-based entity, leveraging the double-extortion technique and exploiting ProxyShell flaws to extort potential targets. THREAT ADVISORY •ATTACK REPORT (Red) 2 | CVE Table CVE NAME PATCH CVE .
New LV Ransomware Variant Hijacks Malicious Binaries Used by REvil Operators. The LV variant operators have been observed in the wild since October 2020, deploying a tweaked version of REvil’s binary with references to REvil’s C2 . The Trend Micro research team recently analyzed an infection related to the LV ransomware group, a ransomware as a service (RaaS) operation that has been active since late 2020, and is reportedly based on REvil (aka Sodinokibi). CTU analysis revealed that the LV ransomware is not a distinct ransomware family; it is repurposed REvil ransomware. By modifying the binary of a prolific ransomware family, the GOLD NORTHFIELD threat actors significantly expedited their . Researchers have discovered that the LV ransomware that has been in use since late 2020 is actually a modified version of the REvil ransomware binary that is being distributed by a separate threat group.
In what can be described as a case of piracy among cybercrime gangs, the LV ransomware gang appears to have hijacked and modified the binary payload of the more infamous REvil group. German power electronics manufacturer Semikron has disclosed that it was hit by a ransomware attack that partially encrypted the company's network.
Trend Micro provides a detailed analysis of an LV ransomware attack on a Jordan-based company, highlighting the attackers' methods and the wide range of targeted industries.
Researchers at Secureworks tracked what looked like a new ransomware strain, dubbed LV, which has been in the wild since late 2020, and found that it had identical code structure to REvil.
In an incident, LV Ransomware compromised the corporate environment of a Jordan-based organization. It exploited the Microsoft flaws— ProxyShell and ProxyLogon —vulnerabilities and dropped a webshell in the public access folders.LV ransomware-as-a-service has been active since late 2020. The most recent infiltration entailed the compromise of the corporate environment of a Jordan-based entity, leveraging the double-extortion technique and exploiting ProxyShell flaws to extort potential targets. THREAT ADVISORY •ATTACK REPORT (Red) 2 | CVE Table CVE NAME PATCH CVE .
prada camera bag 2019
lv ransomware hijackers
prada catwalk the complete collectionssusannah frankel 2019
prada men's collection 2019
ganhadores bola prada espn 2019
prada event singapore 2019
Choose your favorite Long Sleeve Grim Reaper-inspired shirt style: v-neck or crew neckline; short, baseball or long sleeve; slim or relaxed fit; light, mid, or heavy fabric weight. Moisture-wicking active t-shirts are here, too. T-shirt colors are available in the best-selling black, the classic white, and many others.
lv ransomware|lv ransomware gang revil